Credits and sources
Microsoft Learn
https://learn.microsoft.com/en-us/azure/defender-for-cloud/security-policy-concept https://learn.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controlsIntro
In this part of the blog series, I want to show you how to remediate or dismiss the recommendation that Microsoft provides. Most of the recommendations are something you will want to implement, but some recommendations might not fit your environment. There are multiple ways of dismissing the recommendation. Here I will show you two, one is to waive the recommendation, and the other is to disable the policy that provides the recommendation. I won’t show how I go about all recommendations in this post, but I will show you how to use the security posture to improve your Azure secure score.
Fix a recommendation
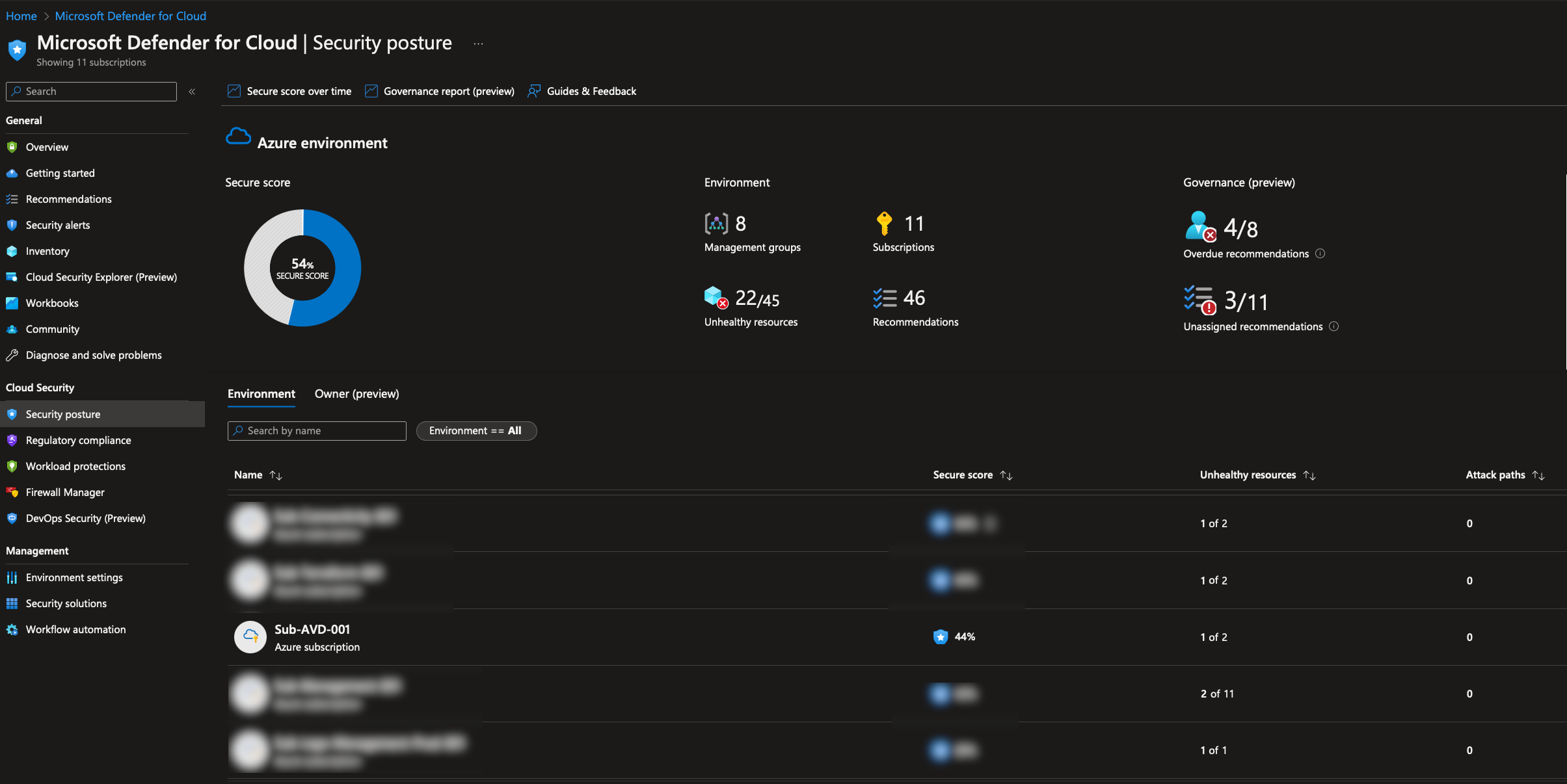
First, lets us fix a recommendation. To do this, I will click “Security posture” and then “View recommendations.”
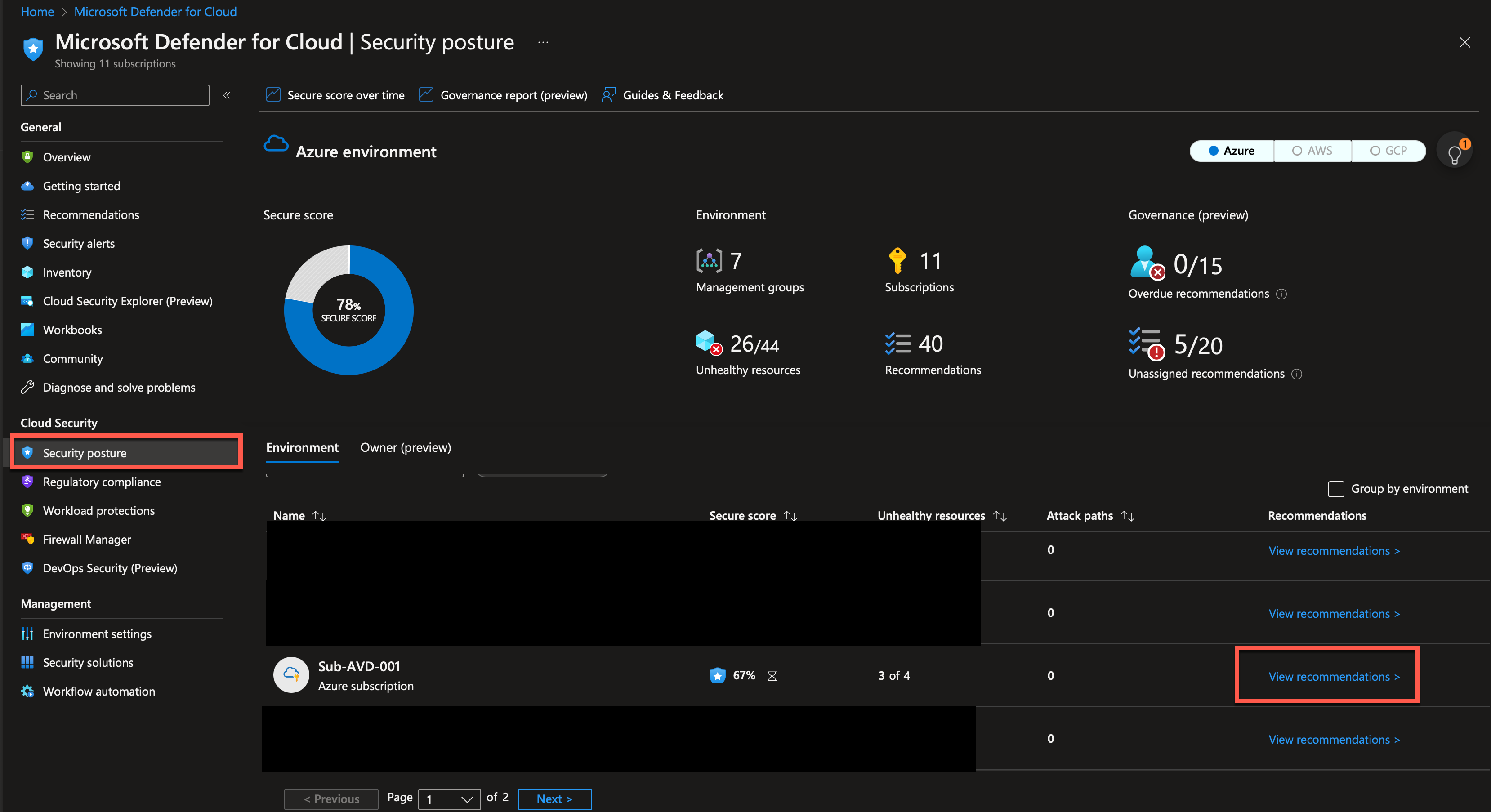
I will select the “Log Analytics agent should be installed on virtual machines.”
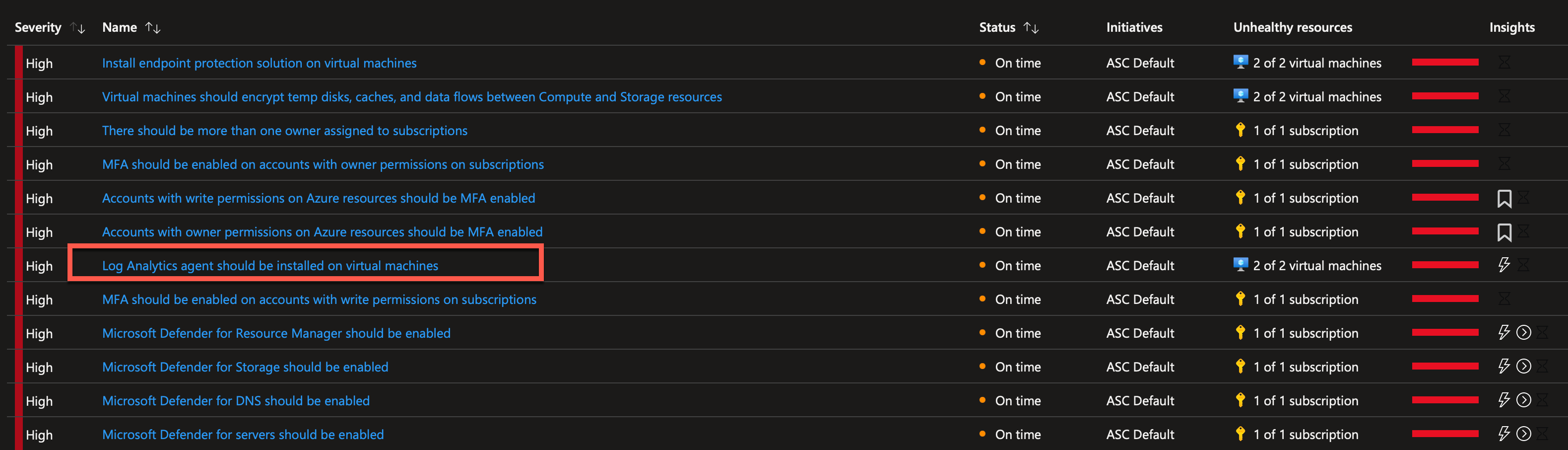
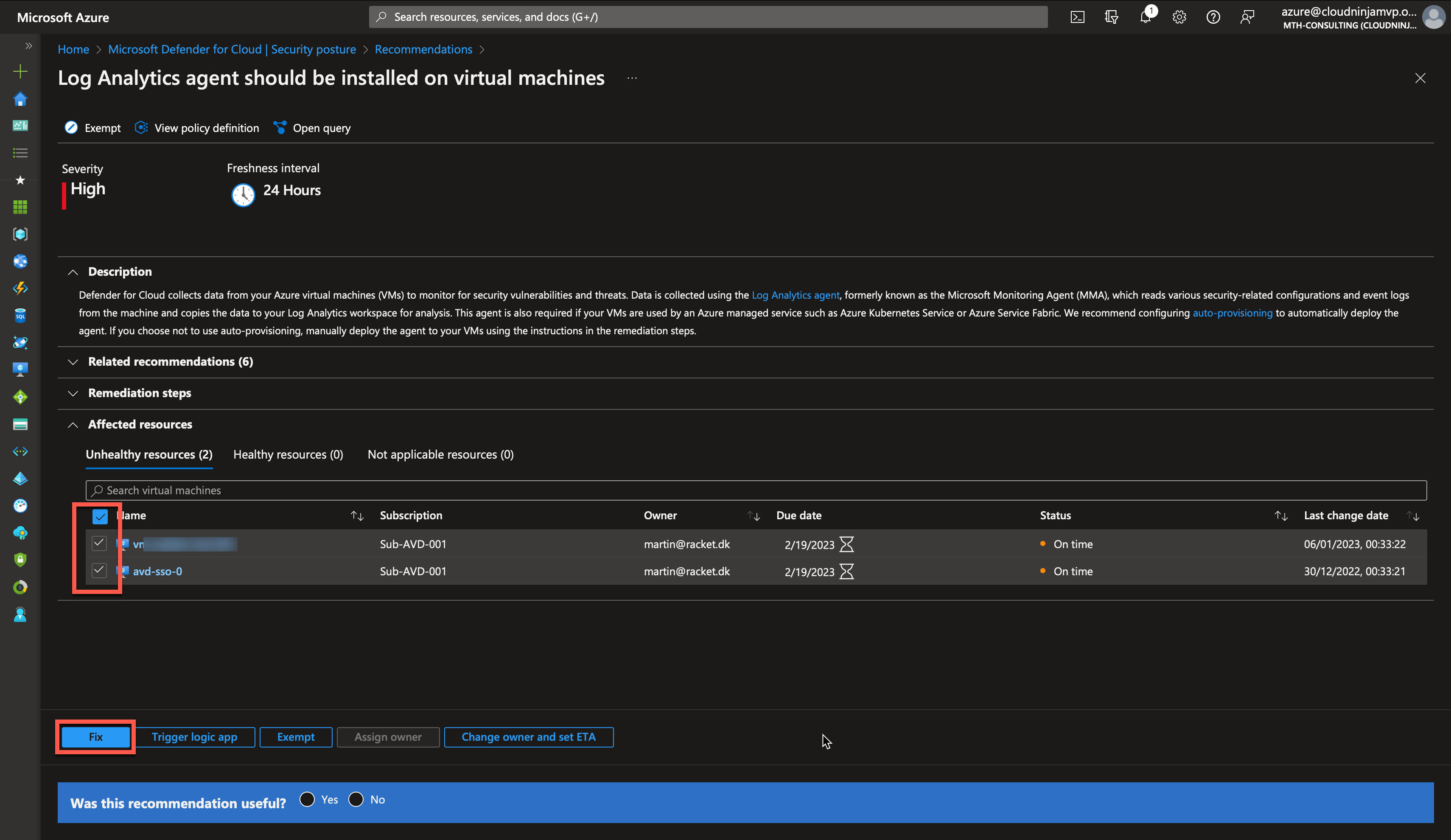
On the next screen, I can see which resources are affected by this policy, and I can also see a description of why it is recommended to have a Log Analytics agent on my machines.
I will mark both my machines and click on “Fix.”
The guide shows me the remediation steps. I choose my Log Analytics Workspace and click “Fix 2 resources.”
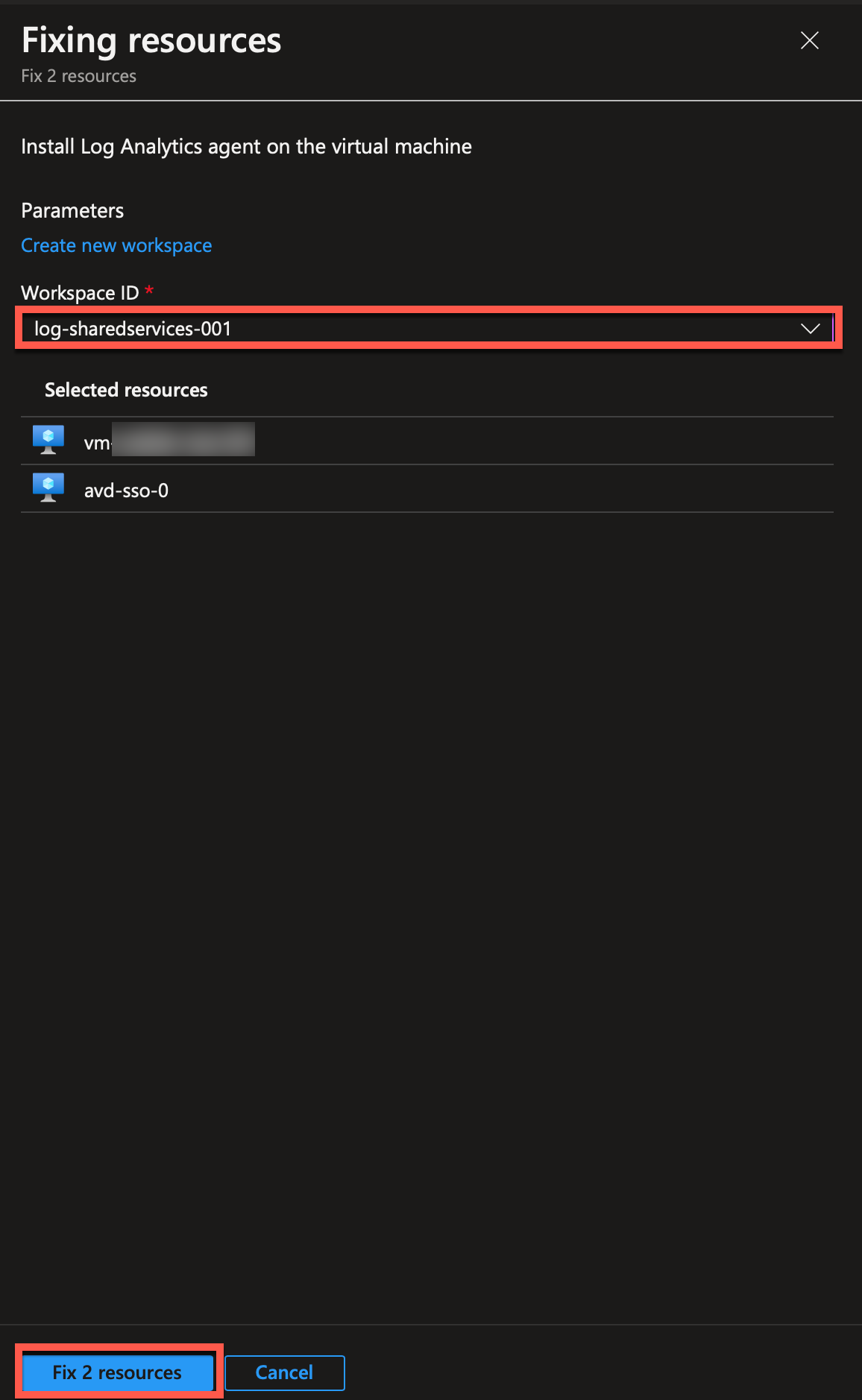
The remediation will run as a task, and when complete, I can see if the task was successful or not.
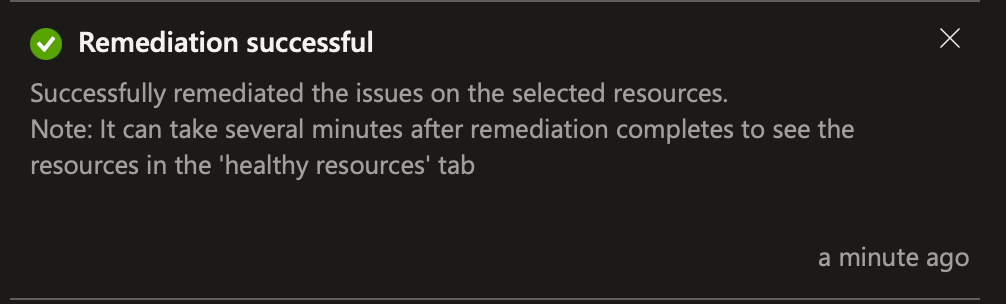
Recommendation without a fix option
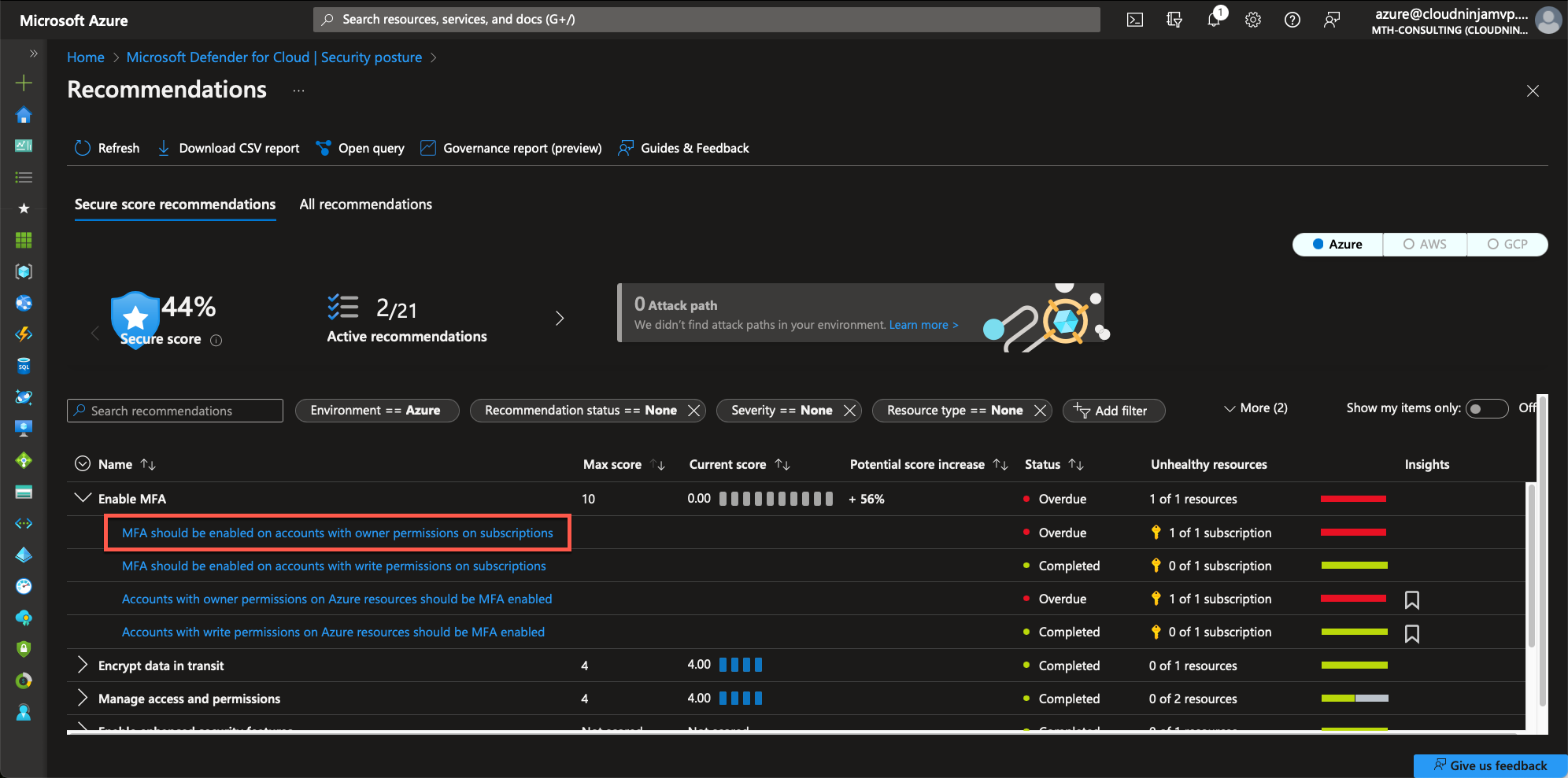
Not all recommendations come with a fix button. Some policies will require you to change the configuration in your environment manually. One of these recommendations is the MFA requirement. Here I will show you want it looks like, but I won’t guide you through enabling MFA for your users. Please let me know if you would like me to write a post on that.
I will click “MFA should be enabled on accounts with owner permissions on subscriptions.”
Here, I will expand the “Remediations steps” and read through the steps needed.
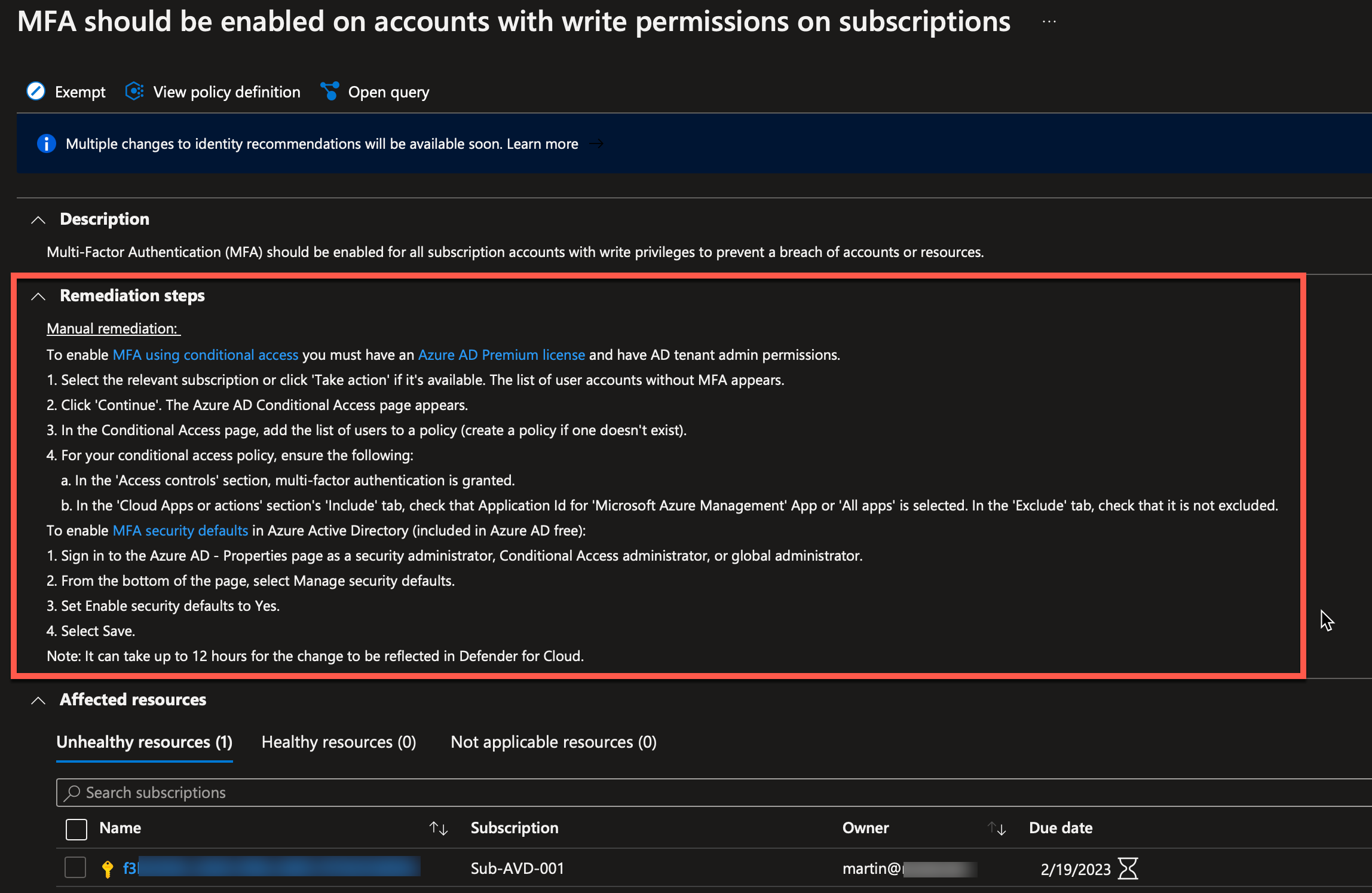
If I click on the subscription, I can see which owners are affected by the policy, and then I can ensure that I get MFA enabled for these users.
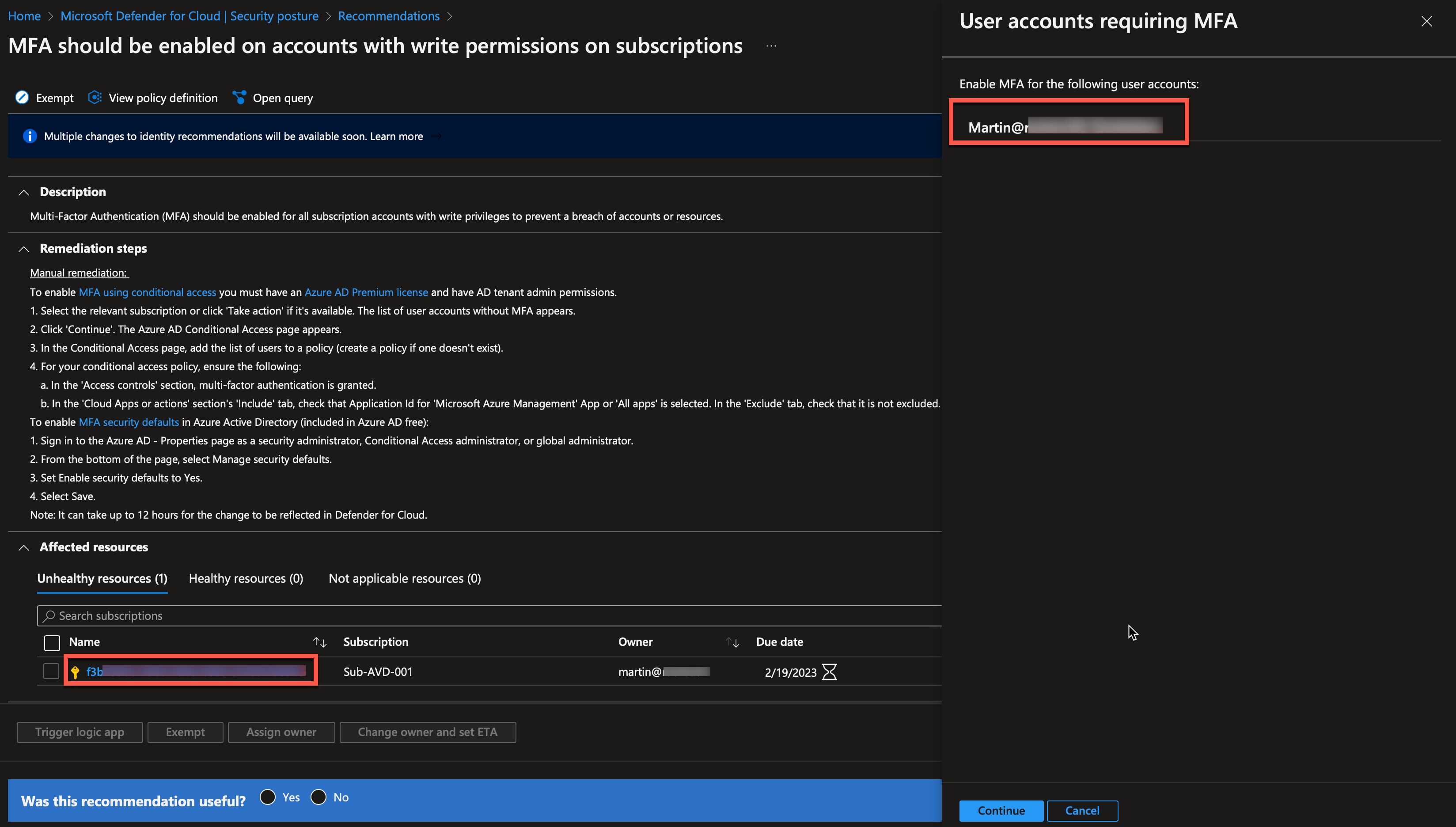
I can consider my work done when I have completed the remediations steps, but the secure score won’t update immediately.
Waiver a recommendation
If Microsoft has a recommendation you don’t want to implement for a specific subscription, you can waive the recommendation. To do this, we follow almost the same process as above, but instead of fixing, we will waive the risk.
Here, I will waive the “Virtual networks should be protected by Azure Firewall,” this is just an example since I usually recommend having an Azure Firewall in front of an AVD environment.
Next, I will mark my virtual network and click the “Exempt” button.
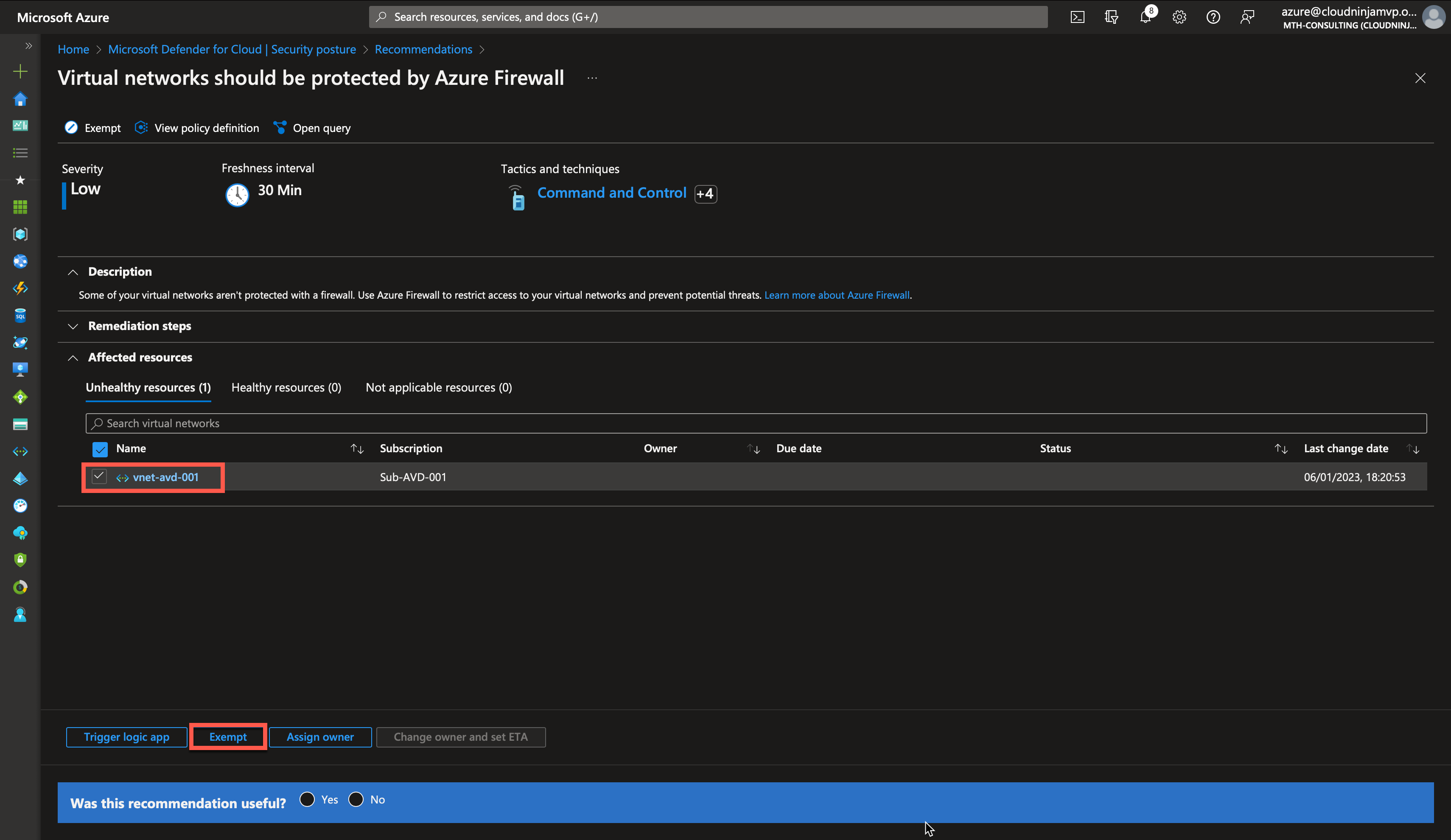
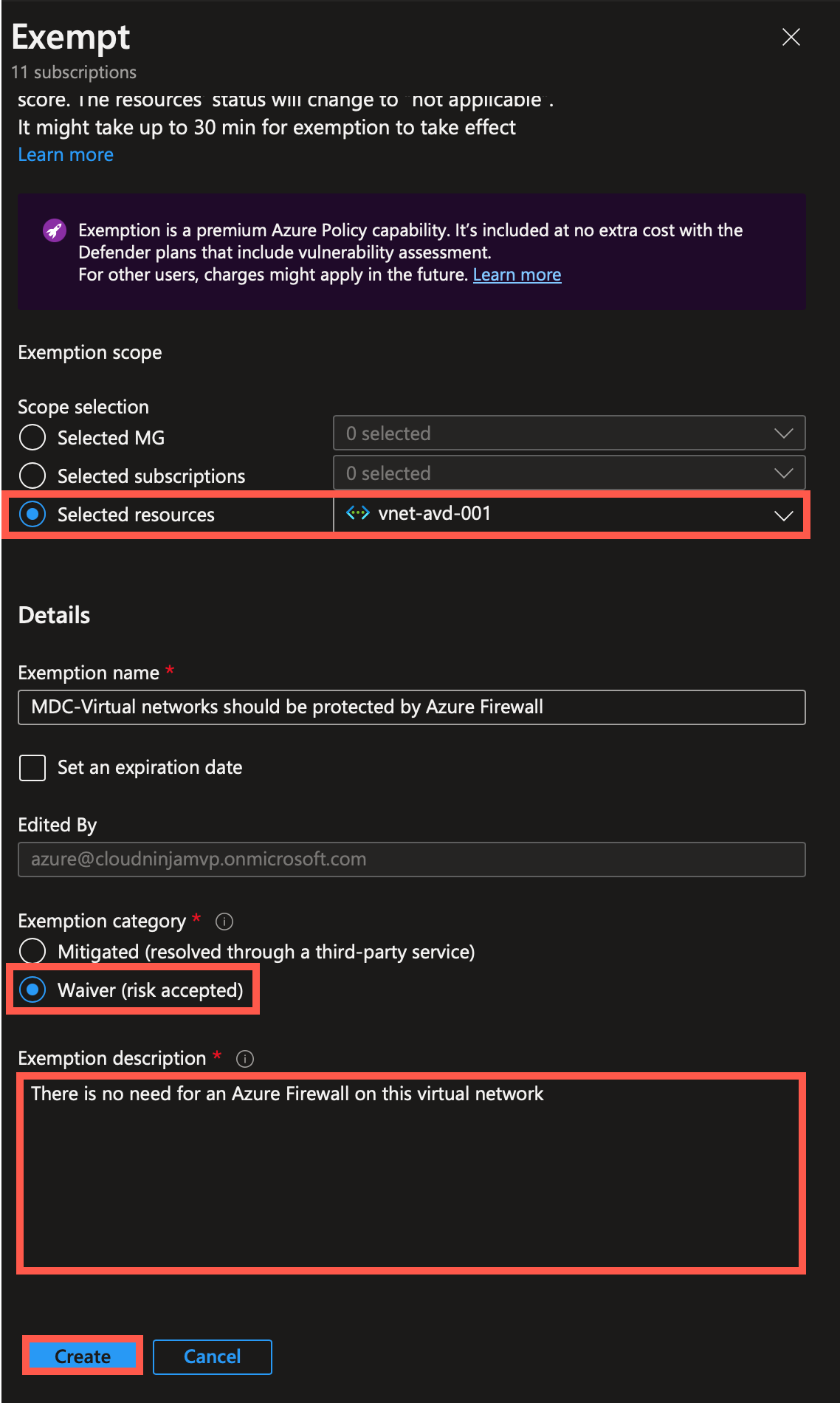
The exemption scope is automatically selected, but ensure that it is correct. Next, I will choose “Waiver (risk accepted)” and then provide a reason for the exemption. In this case, I state that no Azure Firewall is needed for this virtual network. One important thing to notice is that you can set an expiration on the exemption. If you know this exemption is temporary, select the expiration date, and Defender for Cloud will warn you if the policy is not compliant after expiry.
I clicked “Create” to accept the policy is not part of the secure score.
Disable policy
If none of your subscriptions should be affected by a specific policy, you can disable that policy in the security benchmark assignment. To do this, I will go to my Azure Policies, but searching for “Policy,” and click on “Policy.”
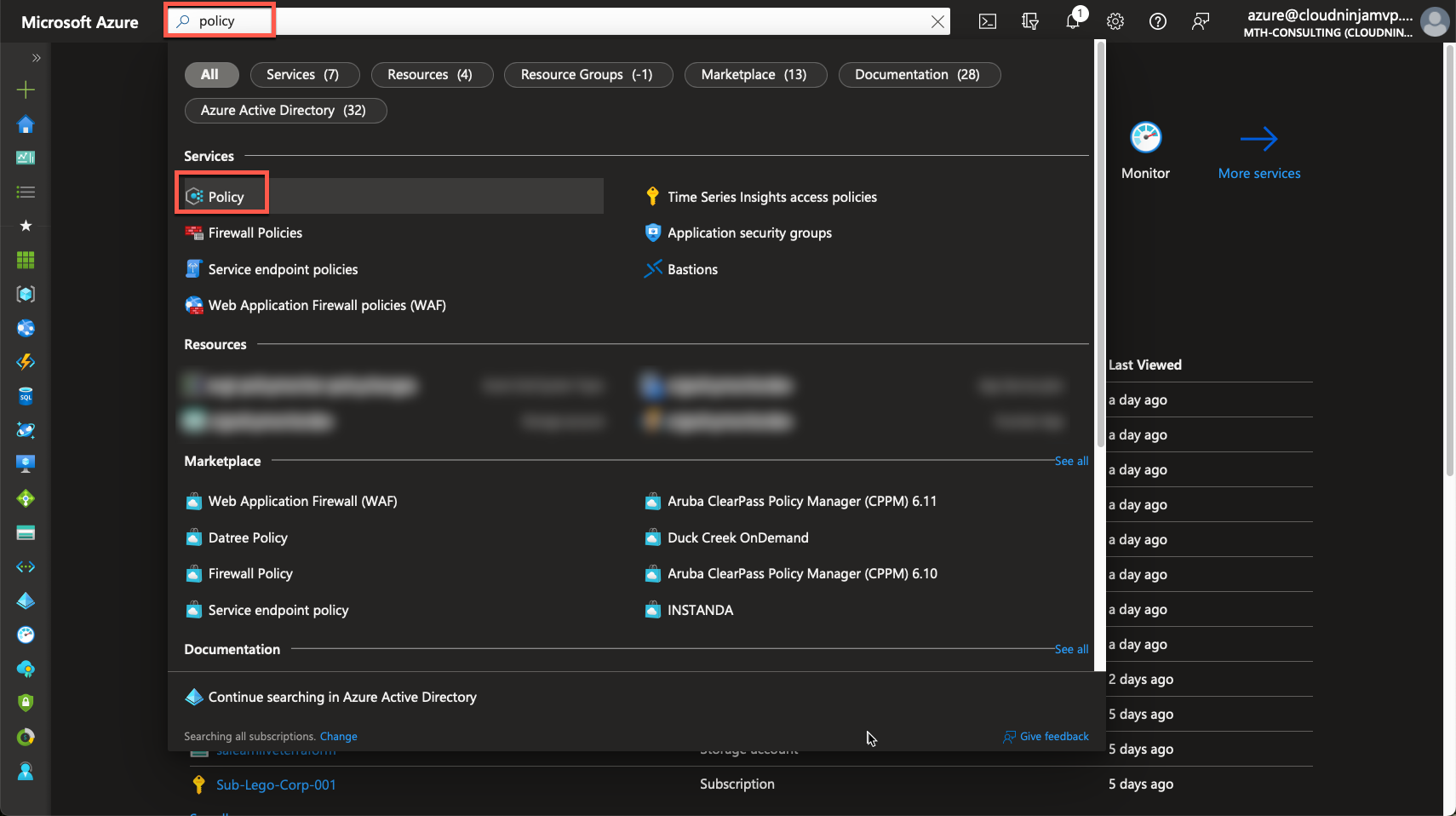
In this case, I will set my scope to the subscription I am working with, “Sub-AVD,” and then click on the ASC policy.
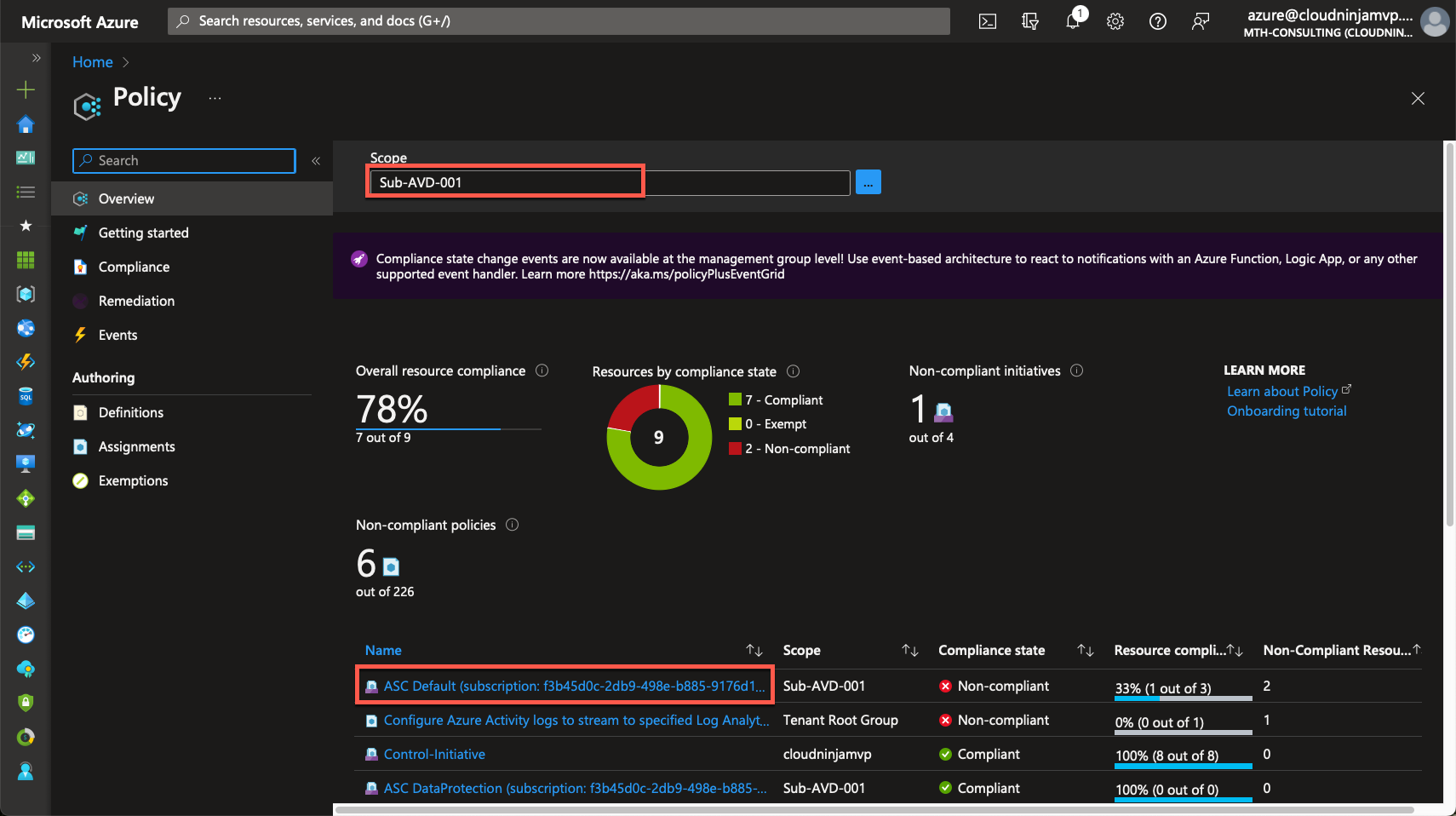
Here, I can go to “Edit assignment.”
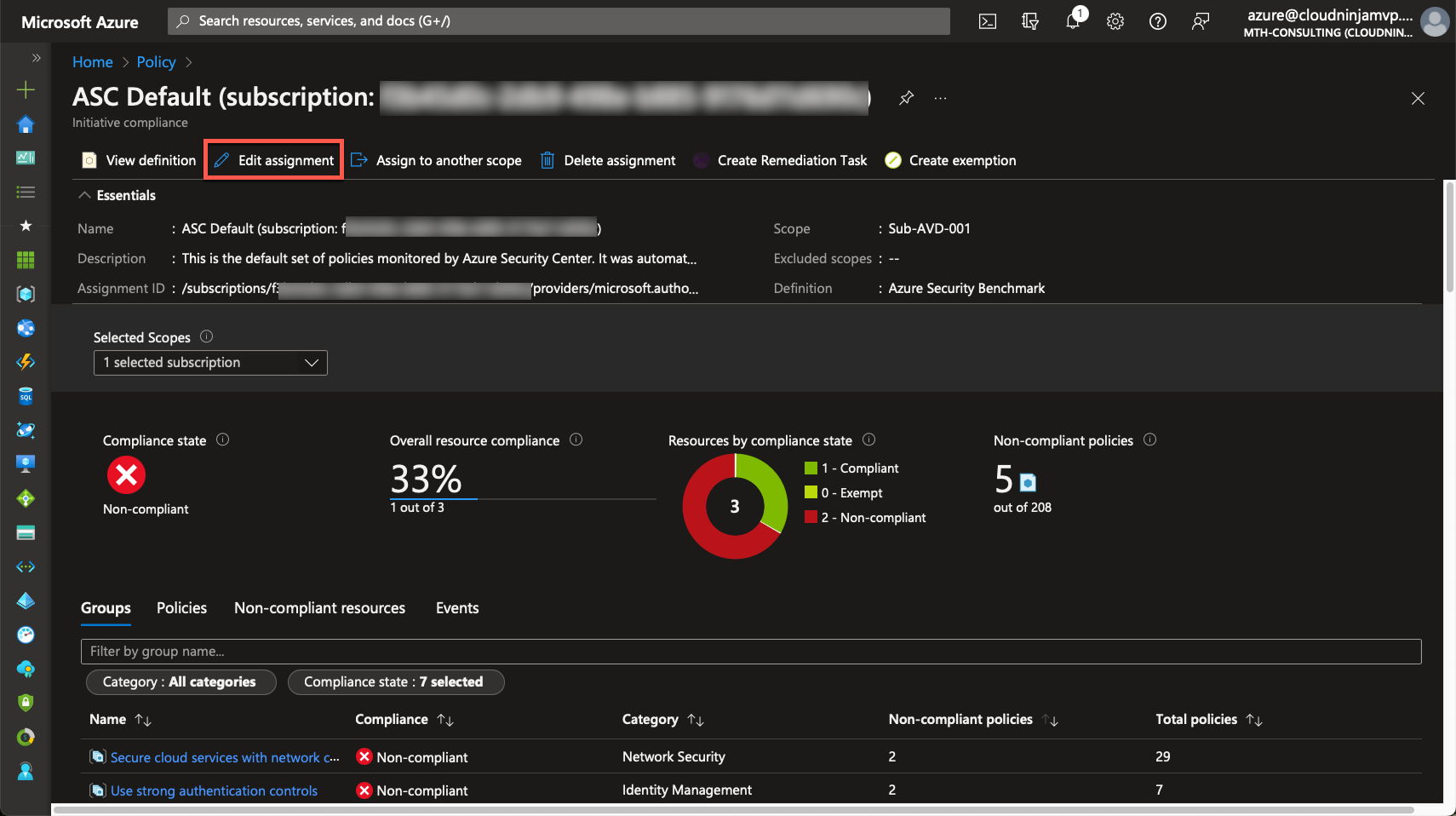
I go to the “Parameters” tab and remove the checkmark.
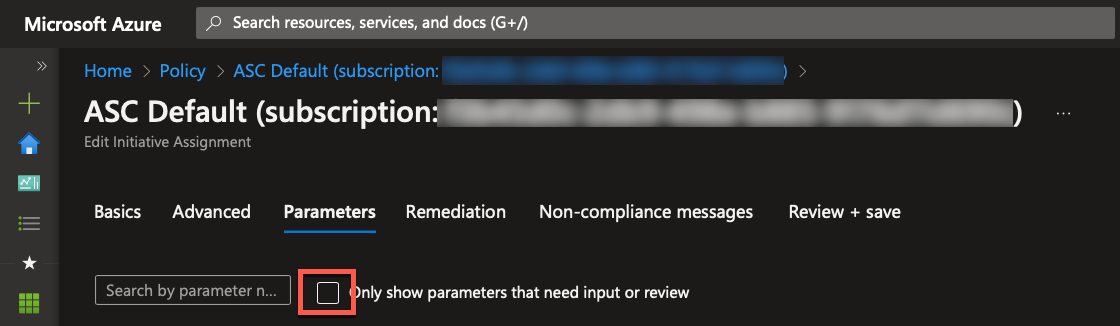
A list of all the policies that Microsoft has included in the security benchmark will show up. I can now search or browse for the policy I want to disable. In my case, I have selected “There should be more than one owner assigned to your subscription,” and I have chosen “Disabled” in the drop-down box.
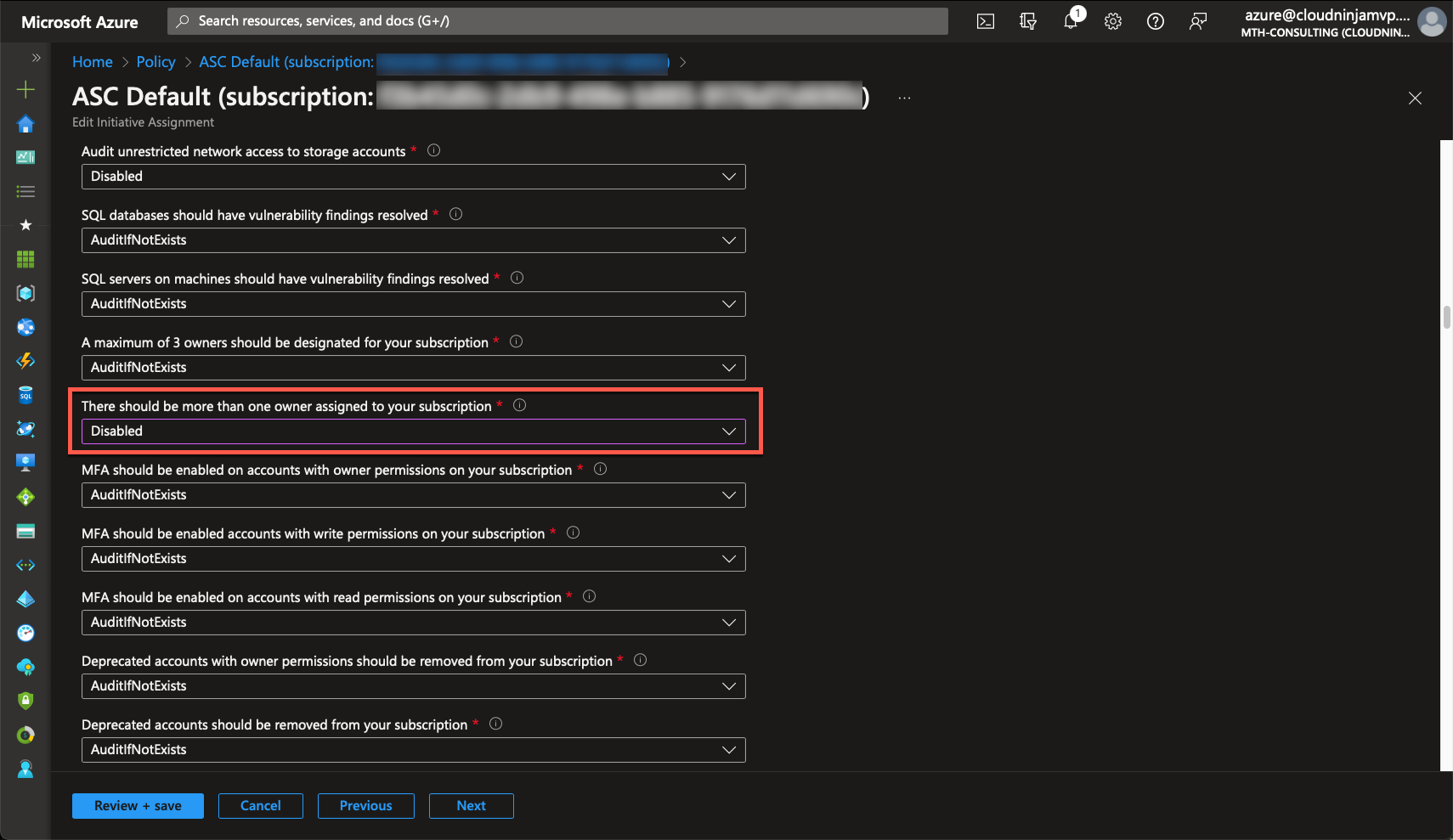
When I have modified the wanted policies, I will click “Review + save” and then “Save.”
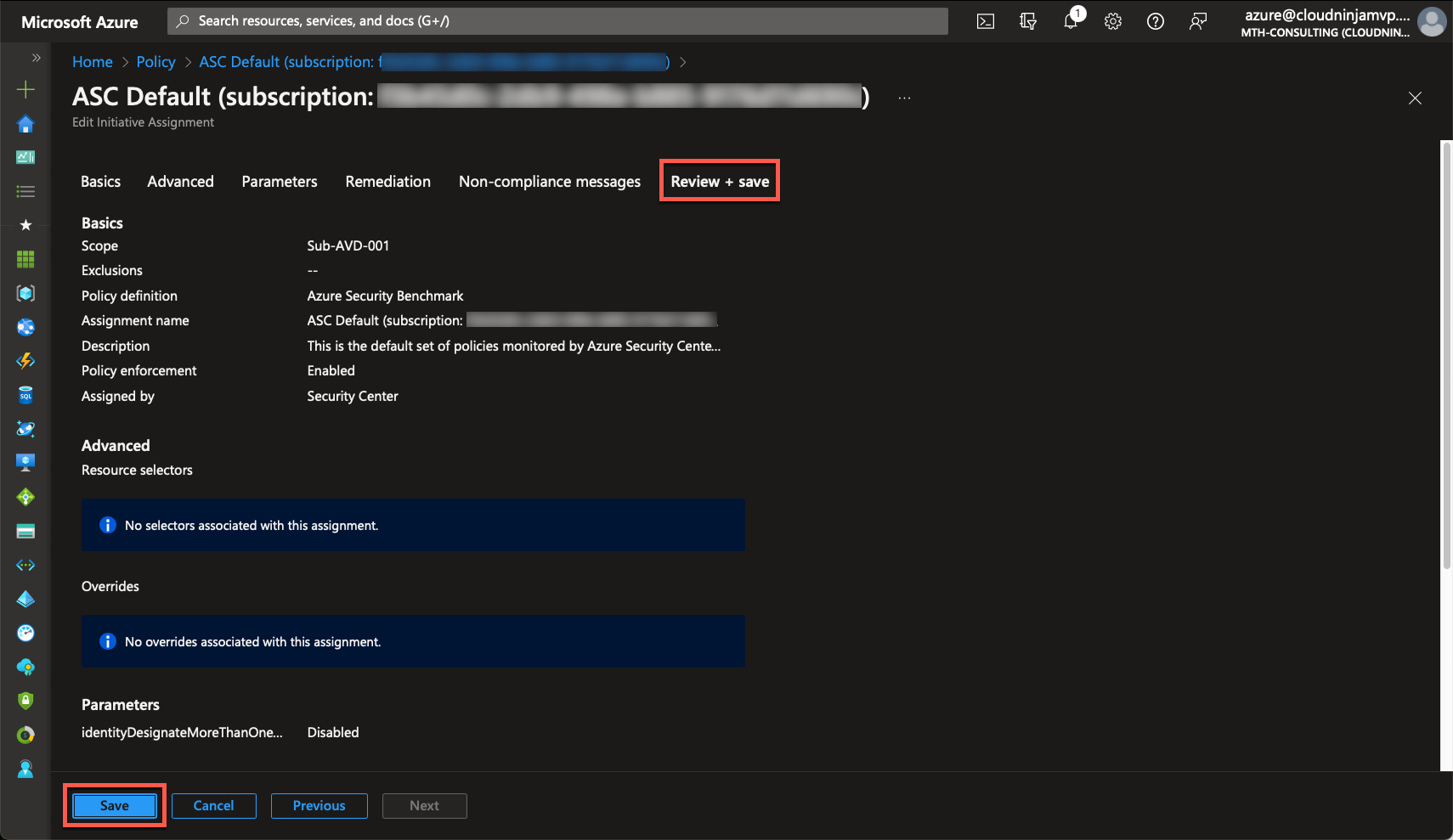
With this modification, Microsoft will ignore the disabled policies, and they will not count as a negative in the secure score.
Conclusion
We now know how to remediate, fix, waive, and disable recommendations in Defender for Cloud. With this knowledge, your cloud security score will be high, and your environment is likely more secure now than when you started. This score, however, is not meant to be the end of your security work. Microsoft is providing some help to improve your security, but it is your responsibility always to keep your Azure environment secure. In the blog series, we still have more parts where I will show more of the tools Microsoft provides to help you on your road to a secure Azure workload.
Join me in the next part of the blog series. This post will be about Defender for DNS and will be the first workload protection subject in the series.